ANTIDDOS CWP Panel (Update 2018 - How to full install)
STEP 1: Install CWP Panel
cd /usr/local/src
wget http://centos-webpanel.com/cwp-el7-latest
sh cwp-el7-latestMore documentation:
http://centos-webpanel.com/cwp-installationSTEP 2: Install vDDoS Proxy Protection
vDDoS Proxy Protection is free software to provide a Reverse Proxy Server HTTP(S) protocols. It act as a Filter & Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack to protect your website.
curl -L https://github.com/duy13/vDDoS-Protection/raw/master/latest.sh -o latest.sh
chmod 700 latest.sh
bash latest.shSTEP 3: Change Apache Default Port
By default, CWP uses Apache alone and runs on port 80, 443. We can use the function:
Setup default Web Servers at Apache Settings >> Select WebServer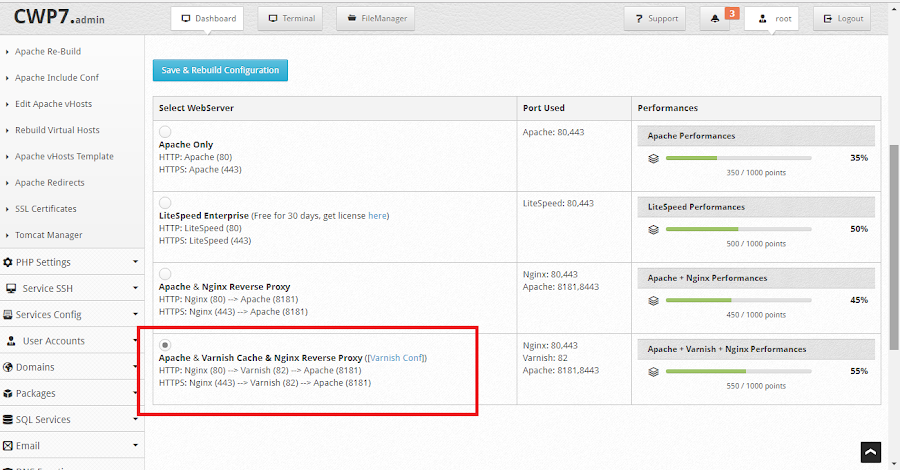
Change it into:
Apache & Varnish Cache & Nginx Reverse Proxy or
Apache & Nginx Reverse Proxy, So Apache will be listened to at another port is 8181 and 8443; to facilitate our proxying.
Click Save and Re-check Apache port:
[root@vDDoS-CWP Panel ~]# netstat -lntup|grep httpd; netstat -lntup|grep nginx; netstat -lntup|grep varnishd
tcp6 0 0 :::8181 :::* LISTEN 1304/httpd
tcp6 0 0 :::8443 :::* LISTEN 1304/httpd
tcp 0 0 1.2.3.4:80 0.0.0.0:* LISTEN 5481/nginx: master
tcp 0 0 1.2.3.4:443 0.0.0.0:* LISTEN 5481/nginx: master
tcp 0 0 127.0.0.1:6082 0.0.0.0:* LISTEN 1418/varnishd
tcp 0 0 0.0.0.0:82 0.0.0.0:* LISTEN 1418/varnishd
tcp6 0 0 :::82 :::* LISTEN 1418/varnishd
It can be seen that Nginx listened at 80 and 443, then it proxyed to port 82 of Varnish cache server then Varnish continued forwarding traffic to Apache at port 8181.
So you can stop Nginx and replacing it with vDDoS, Reverse Proxy for vDDoS to any port of Apache or Varnish (With Varnish you will be cached and reach faster speeds)
service nginx stop
chkconfig nginx offSTEP 4: Config vDDoS Proxy Protection
The following example assumes the IP address of the server you are 1.2.3.4:
nano /vddos/conf.d/website.conf
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://0.0.0.0:80 http://1.2.3.4:8181 no no no no
default https://0.0.0.0:443 http://1.2.3.4:8181 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crtConfiguration like the above you will use directly from vDDoS reverse proxy to Apache port, If you want to use port of Varnish cache server then you can configure as follows:
nano /vddos/conf.d/website.conf
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://0.0.0.0:80 http://1.2.3.4:82 no no no no
default https://0.0.0.0:443 http://1.2.3.4:82 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
Restart vDDoS service after you have configured:
/usr/bin/vddos restart
Auto-start vDDoS services on boot:
/usr/bin/vddos autostart
STEP 5: Config vDDoS Auto Add
vDDoS Auto Add is a addon support for vDDoS Proxy Protection - Monitor Domains/Aliasdomains/Subdomains in Panel Hosting, Web Server, List Domain, Virtual Host... and automatically add them into the website.conf file.
nano /vddos/auto-add/setting.conf
Default Setting for vddos-add command:
SSL Auto
Cache no
Security no
HTTP_Listen http://0.0.0.0:80
HTTPS_Listen https://0.0.0.0:443
HTTP_Backend http://1.2.3.4:82
HTTPS_Backend http://1.2.3.4:82Crontab CWP Panel:
echo '*/25 * * * * root /usr/bin/vddos-autoadd panel cwp apache' >> /etc/crontab
STEP 6: Config vDDoS Auto Switch
vDDoS Auto Switch is a addon support for vDDoS Proxy Protection - Automatically identifies overloaded websites and changes their Security Mode.
echo '*/6 * * * * root /usr/bin/vddos-autoswitch checkalldomain high' >> /etc/crontab
echo '0 */3 * * * root /usr/bin/vddos-autoswitch flushalldomain /vddos/conf.d/website.conf no' >> /etc/crontab