This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
Pages: [1]
1
Installation / Re: Outgoing attacks to randomIPs "After clean cwp insallation"
« on: December 22, 2022, 07:53:36 PM »
just close all ports but 80 443 mail ssh cwp vb... from firewall (hosting company firewall)
2
Installation / Re: Outgoing attacks to randomIPs "After clean cwp insallation"
« on: December 09, 2022, 12:20:46 PM »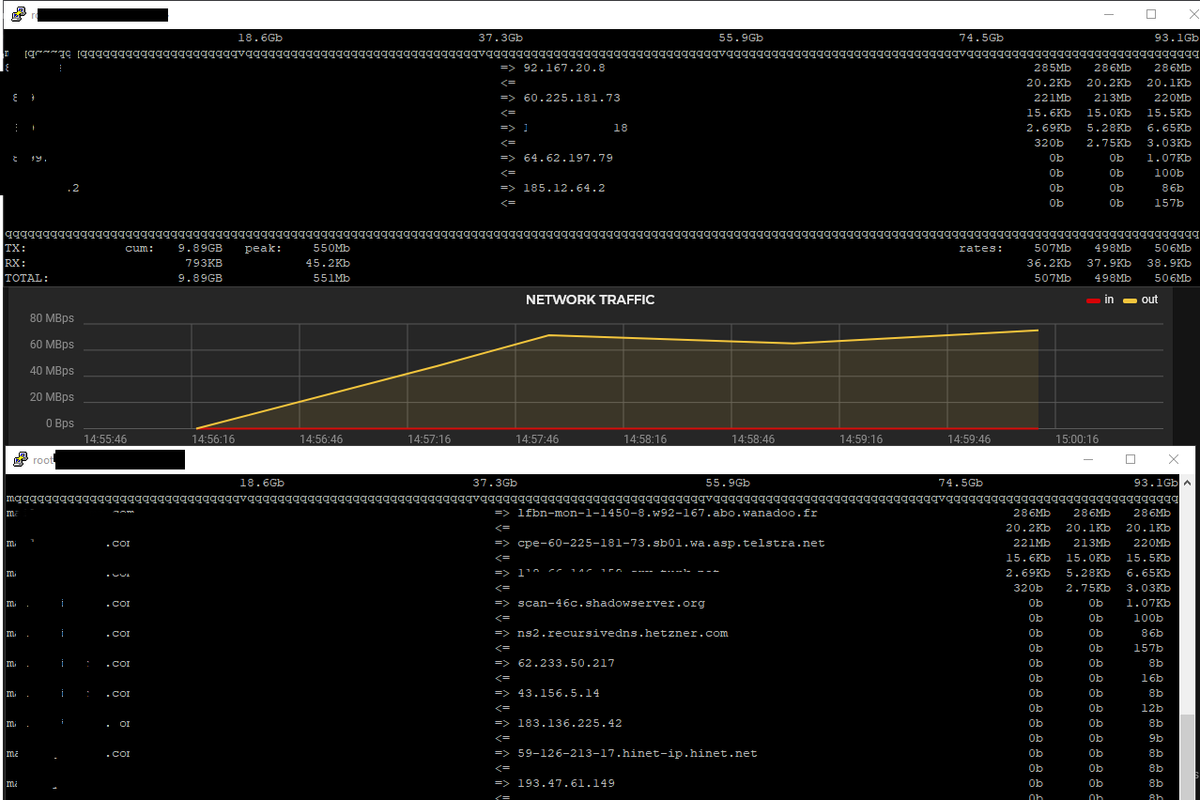 rebuild and clean installation (again, after i post my first message) iftop iftop -n
rebuild and clean installation (again, after i post my first message) iftop iftop -n
3
Installation / Outgoing attacks to randomIPs "After clean cwp insallation"
« on: December 09, 2022, 08:36:56 AM »
1 week ago I do clean installation centos7 with centos web panel but I dont transfer my website and i dont start using this vps...
Vps created and builded with centos7 from Hetzner panel / new vps server with new ip (not blacklisted) maybe not used from long time ago.
- A few hours later i receive abuse warning mail from Hetzner and i see "17 TB traffic outgoing" used by my vps.
(i never see up 100gb/per month in my life... and this vps not host website.)
- I check server logs, php files, nothing wrong and no one enter my vps via ssh/ftp or cwppanel.
I do malware scan, clamav scan, rkhunter scan, chrootkit scan nothing found, no virus/exploit detected.
I format and rebuild my vps again but iftop screen same as old, i create new ip different vps and do same installation, same attacks happen again my fresh build vps attacking random ips.
When i power-on attacks start again
hetzner panel:
ssh iftop: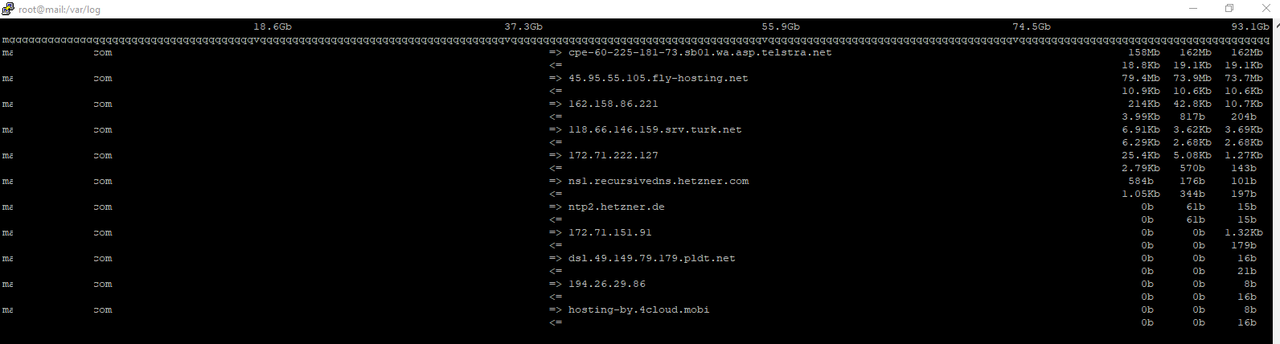
a few hours later
hetzner panel: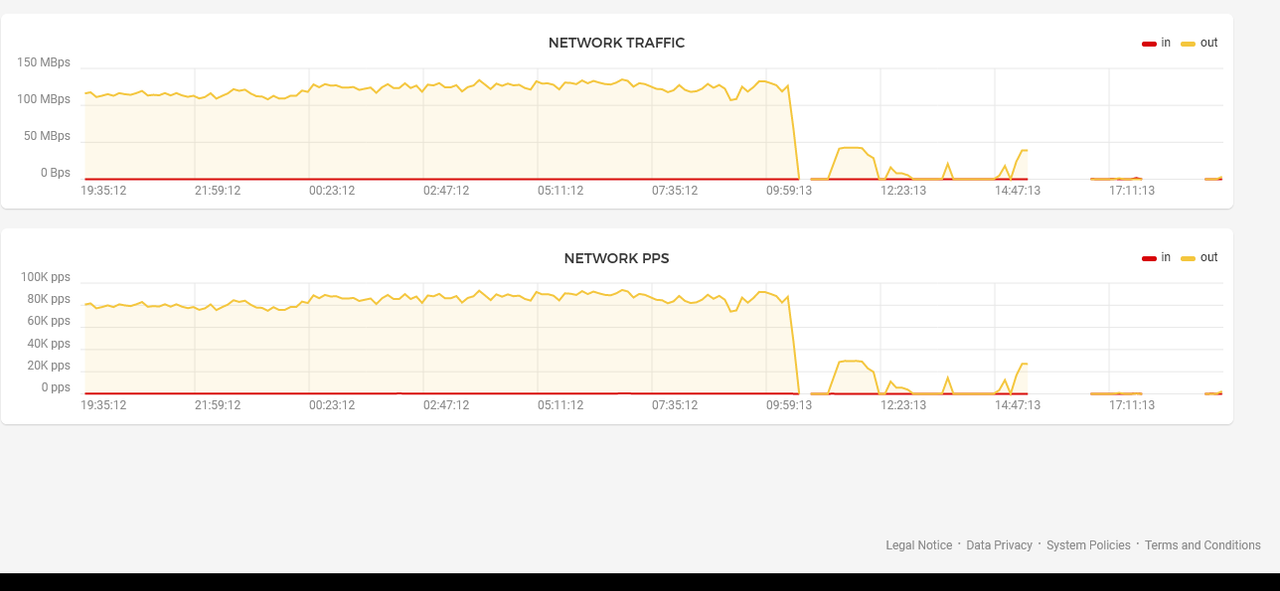 (breaks=vps stopped)
(breaks=vps stopped)
ssh iftop: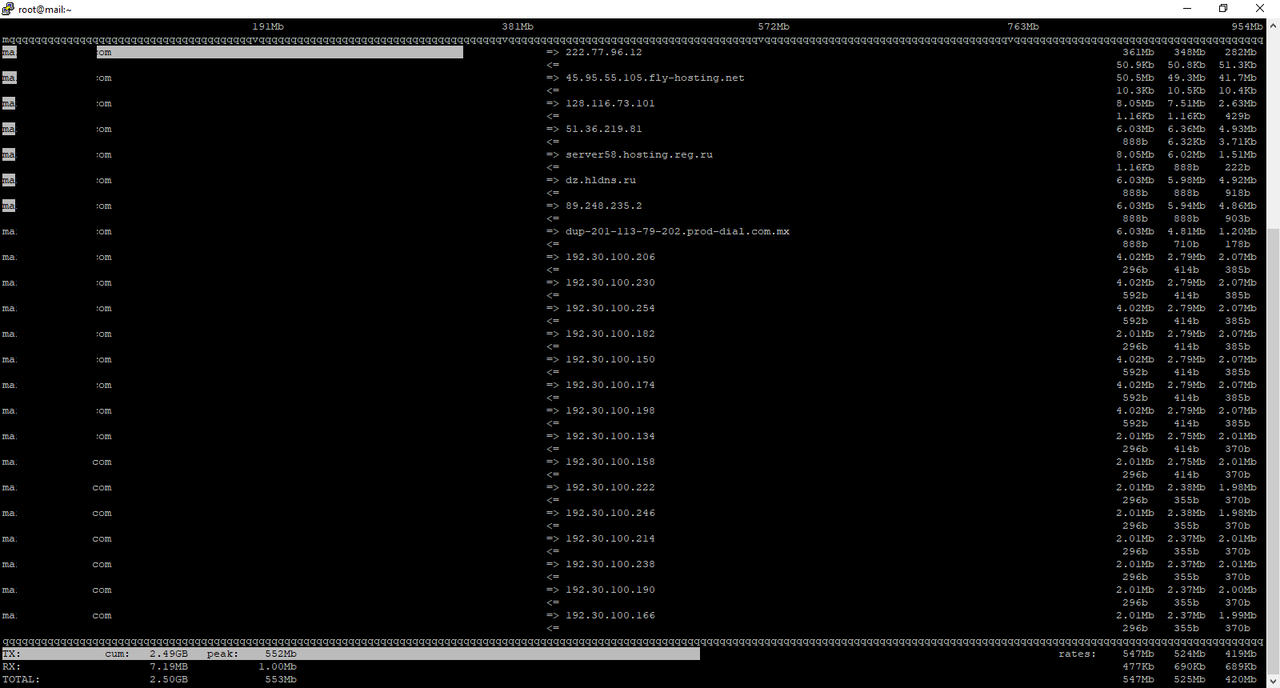
When i create firewall rule from Hetzner panel (incoming 80 8080 53 (deny all other ports)) attacks stop
I think my vps has exploit or virus and i dont do anything but installing cwp...
Could i be missing something, do you have any advice that can help me with this?
Thank you.
Vps created and builded with centos7 from Hetzner panel / new vps server with new ip (not blacklisted) maybe not used from long time ago.
- A few hours later i receive abuse warning mail from Hetzner and i see "17 TB traffic outgoing" used by my vps.
(i never see up 100gb/per month in my life... and this vps not host website.)
- I check server logs, php files, nothing wrong and no one enter my vps via ssh/ftp or cwppanel.
I do malware scan, clamav scan, rkhunter scan, chrootkit scan nothing found, no virus/exploit detected.
I format and rebuild my vps again but iftop screen same as old, i create new ip different vps and do same installation, same attacks happen again my fresh build vps attacking random ips.
When i power-on attacks start again
hetzner panel:

ssh iftop:

a few hours later
hetzner panel:
 (breaks=vps stopped)
(breaks=vps stopped)ssh iftop:

When i create firewall rule from Hetzner panel (incoming 80 8080 53 (deny all other ports)) attacks stop
I think my vps has exploit or virus and i dont do anything but installing cwp...
Could i be missing something, do you have any advice that can help me with this?
Thank you.
4
iptables / Re: ssh brute force attacks to random ports/users
« on: April 01, 2022, 02:00:37 PM »Using a firewall is required, but so long as the port is open, you are subject to brute force attacks. Hence why I say using a iptables firewall manager such as CSF/LFD.as i say. csf or lfd or ip ip/subnet banning is not solution. thank you.
The software does the same thing you are doing manually, except it can monitor the log files and set bans on IP's that are trying to brute force.
IF you want to exclusively use cloudflare, you could open those ports to ONLY cloudflare's IP Range, and shut it off to everything else.
CWP supports the software it bundles, not every underlying software that comes with it. You can try the paid support, but I'm afraid you'll receive the same response.
I'm sorry, but the only two solutions I can give are either use CSF/LFD with automated banning, or close the firewall to everything but cloudflare and select IP's. Any other solution is out of the scope of this forum. Thank you for understanding.
solution2:
i close all ports but necessary:
use this commands from ssh console.
iptables -A INPUT -m conntrack -j ACCEPT --ctstate RELATED,ESTABLISHED
iptables -A INPUT -p tcp -m tcp -m multiport -m state --state NEW -j DROP ! --dports 22,80,443,8181,8443,25,587,465,110,995,143,993,11211
5
iptables / Re: ssh brute force attacks to random ports/users
« on: March 31, 2022, 06:56:12 PM »
update.
sol1
sol2
tested but not fix...
i think i read my securelogs wrong and scanner/bot not requests to "random" ports...
(i will update topic again)
sol1
Quote
############310322--closing all ports but these
# Set the default policy of the INPUT chain to DROP
# Accept incomming TCP connections from eth0 on port 80 and 443
#www
#-A INPUT -i eth0 -p tcp --dport 80 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 443 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 8181 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 8443 -j ACCEPT
#ssh
#-A INPUT -i eth0 -p tcp --dport 22 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 25 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 587 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 465 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 110 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 995 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 143 -j ACCEPT
#-A INPUT -i eth0 -p tcp --dport 993 -j ACCEPT
############310322--closing all ports but these
sol2
Quote
iptables -A INPUT -m conntrack -j ACCEPT --ctstate RELATED,ESTABLISHED
iptables -A INPUT -p tcp -m tcp -m multiport -m state --state NEW -j DROP ! --dports 22,80,443,8181,8443,25,587,465,110,995,143,993,11211
tested but not fix...
i think i read my securelogs wrong and scanner/bot not requests to "random" ports...
(i will update topic again)
6
iptables / Re: ssh brute force attacks to random ports/users
« on: March 31, 2022, 08:06:52 AM »You should be using csf firewall /etc/csf/csf.conf
Using iptables directly can cause you serious issues if you do something wrong. Plus using CSF, you have LFD: Look for the below options in csf.conf
RESTRICT_SYSLOG = "3"
LF_SSHD = "5"
LF_SSHD_PERM = "1"
i dont want to use csf or other firewall. this is not main problem. in www i am using cloudflare already but this bot attacks directly to server ip from tcp/ssh. i think its automated brute force attack bot and probably not only targeting my server. scans all the internet.
Thank you.
- As i say they have unlimited proxy, banning is not solution! web users comes from behind cloudflare. i can ban all the world ips but cloudflare but it doesnt make sense.
"i need to close all ports but necessary ones like http ssh mail/pop etc."
Thank you for helping.
7
iptables / Re: ssh brute force attacks to random ports/users
« on: March 30, 2022, 10:36:37 PM »
can i block all ports but www mail ssl ssh (and other must remain open) ports from iptales ?
Thank you
I was about to ask if you had a firewall and then I read this part. Why have you not done this already? The standard practice for server protection is to block all ports except those you want to be open.
What OS is this?
Quote
Distro Name: CentOS Linux release 7.9.2009 (Core)
Kernel Version: 5.16.13-x86_64-linode153
Platform: x86_64 kvm
I dont change anything i dont open all ports (am i?)
Quote
# Generated by iptables-save v1.4.21 on Thu Mar 31 01:33:43 2022
*security
:INPUT ACCEPT [288520253:87180682456]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [288399815:96551497619]
COMMIT
# Completed on Thu Mar 31 01:33:43 2022
# Generated by iptables-save v1.4.21 on Thu Mar 31 01:33:43 2022
*raw
:PREROUTING ACCEPT [288533873:87181450964]
:OUTPUT ACCEPT [288399815:96551497619]
COMMIT
# Completed on Thu Mar 31 01:33:43 2022
# Generated by iptables-save v1.4.21 on Thu Mar 31 01:33:43 2022
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
# Completed on Thu Mar 31 01:33:43 2022
# Generated by iptables-save v1.4.21 on Thu Mar 31 01:33:43 2022
*mangle
:PREROUTING ACCEPT [288533873:87181450964]
:INPUT ACCEPT [288533873:87181450964]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [288399815:96551497619]
:POSTROUTING ACCEPT [288399815:96551497619]
COMMIT
# Completed on Thu Mar 31 01:33:43 2022
# Generated by iptables-save v1.4.21 on Thu Mar 31 01:33:43 2022
*filter
:INPUT ACCEPT [69639:22040157]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [70263:27924581]
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 25 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 587 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 465 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 110 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 995 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 143 -j DROP
-A INPUT ! -s 127.0.0.0/24 -p tcp -m tcp --dport 993 -j DROP
-A INPUT -p tcp -m tcp --dport 21 -j DROP
-A INPUT -p tcp -m tcp --dport 22 -j DROP
-A INPUT -p tcp -m tcp --dport 23 -j DROP
-A INPUT -p tcp -m tcp --dport 3306 -j DROP
-A INPUT -p tcp -m tcp --dport 3307 -j DROP
-A INPUT -p tcp -m tcp --dport 2030 -j DROP
-A INPUT -p tcp -m tcp --dport 2031 -j DROP
-A INPUT -p tcp -m tcp --dport 2082 -j DROP
-A INPUT -p tcp -m tcp --dport 2083 -j DROP
-A INPUT -p tcp -m tcp --dport 2086 -j DROP
-A INPUT -p tcp -m tcp --dport 2087 -j DROP
-A INPUT -p tcp -m tcp --dport 2095 -j DROP
-A INPUT -p tcp -m tcp --dport 2096 -j DROP
-A INPUT -p tcp -m tcp --dport 19999 -j DROP
-A INPUT -s 143.244.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 202.88.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 45.232.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 223.177.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 194.67.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 49.234.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 222.185.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 157.245.0.0/16 -m comment --comment bruteforce -j DROP
-A INPUT -s 133.167.0.0/16 -m comment --comment bruteforce -j DROP
COMMIT
# Completed on Thu Mar 31 01:33:43 2022
can you see any problem?
8
iptables / ssh brute force attacks to random ports/users
« on: March 30, 2022, 12:21:38 PM »
i change my default server ssh port and i have one ssh user(root)
i see a lot of logs like i quote;
ssh brute force attacks from random ips(proxy worldwide) and random users every day(50.000lines+)
i am sure that attackers dont know my ssh port but they try random ports every time.
i think its autorobot but i want to stop and also i m not using this ports like 6080 37676 43952 ...
-- banning is not solution. can i block all ports but www mail ssl ssh (and other must remain open) ports from iptales ?
-- do you have any ideas to help for me with this?
Thank you
i see a lot of logs like i quote;
Quote
Mar 30 15:09:20 server2 sshd[30568]: Invalid user git from 134.209.212.125 port 37676
Mar 30 15:09:20 server2 sshd[30568]: input_userauth_request: invalid user git [preauth]
Mar 30 15:09:20 server2 sshd[30568]: pam_unix(sshd:auth): check pass; user unknown
Mar 30 15:09:20 server2 sshd[30568]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=134.209.212.125
Mar 30 15:09:22 server2 sshd[30568]: Failed password for invalid user git from 134.209.212.125 port 37676 ssh2
Mar 30 15:09:22 server2 sshd[30568]: Received disconnect from 134.209.212.125 port 37676:11: Bye Bye [preauth]
Mar 30 15:09:22 server2 sshd[30568]: Disconnected from 134.209.212.125 port 37676 [preauth]
Mar 30 15:09:25 server2 sshd[30577]: Address 60.30.98.194 maps to no-data, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Mar 30 15:09:25 server2 sshd[30577]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=60.30.98.194 user=root
Mar 30 15:09:25 server2 sshd[30577]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "root"
Mar 30 15:09:28 server2 sshd[30577]: Failed password for root from 60.30.98.194 port 6080 ssh2
Mar 30 15:09:28 server2 sshd[30577]: Received disconnect from 60.30.98.194 port 6080:11: Bye Bye [preauth]
Mar 30 15:09:28 server2 sshd[30577]: Disconnected from 60.30.98.194 port 6080 [preauth]
Mar 30 15:16:52 server2 sshd[618]: Invalid user prueba from 106.13.209.109 port 43952
Mar 30 15:16:52 server2 sshd[618]: input_userauth_request: invalid user prueba [preauth]
Mar 30 15:16:52 server2 sshd[618]: pam_unix(sshd:auth): check pass; user unknown
Mar 30 15:16:52 server2 sshd[618]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=106.13.209.109
Mar 30 15:16:54 server2 sshd[618]: Failed password for invalid user prueba from 106.13.209.109 port 43952 ssh2
Mar 30 15:16:55 server2 sshd[618]: Received disconnect from 106.13.209.109 port 43952:11: Bye Bye [preauth]
Mar 30 15:16:55 server2 sshd[618]: Disconnected from 106.13.209.109 port 43952 [preauth]
ssh brute force attacks from random ips(proxy worldwide) and random users every day(50.000lines+)
i am sure that attackers dont know my ssh port but they try random ports every time.
i think its autorobot but i want to stop and also i m not using this ports like 6080 37676 43952 ...
-- banning is not solution. can i block all ports but www mail ssl ssh (and other must remain open) ports from iptales ?
-- do you have any ideas to help for me with this?
Thank you
9
CentOS 7 Problems / anacron - cron.daily - mysql restart every night (How to stop ?)
« on: January 22, 2021, 11:13:47 AM »
- I want to stop cron.daily - "mysql restart" command but i dont know how.
(help appreciated. thank you.)
Why ?
i need minimum 2 day uptime for analize mysql conf
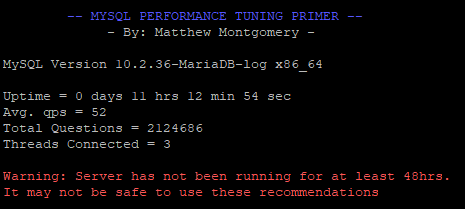
https://i.postimg.cc/mDRydFxg/screenshot-274.png
also(more importantly) sometimes these restarts cause 5++ minutes mysql downtime

https://i.postimg.cc/GppcvXtL/screenshot-273.png

https://i.postimg.cc/cLYN93cD/screenshot-277.png
------------sample-logs--------------------
email
messages logs
cron logs
mysql logs
-------------logs--------------------
(help appreciated. thank you.)
Why ?
i need minimum 2 day uptime for analize mysql conf

https://i.postimg.cc/mDRydFxg/screenshot-274.png
also(more importantly) sometimes these restarts cause 5++ minutes mysql downtime

https://i.postimg.cc/GppcvXtL/screenshot-273.png

https://i.postimg.cc/cLYN93cD/screenshot-277.png
------------sample-logs--------------------
Quote
Anacron job 'cron.daily' on sitename123.com
messages logs
Quote
Jan 10 03:30:01 servername123 systemd: Stopping MariaDB 10.2.36 database server...
Jan 10 03:30:03 servername123 systemd: Stopped MariaDB 10.2.36 database server.
Jan 10 03:30:04 servername123 systemd: Starting MariaDB 10.2.36 database server...
Jan 10 03:30:05 servername123 mysqld: 2021-01-10 3:30:05 140584771946688 [Note] /usr/sbin/mysqld (mysqld 10.2.36-MariaDB-log) starting as process 18309 ...
Jan 10 03:30:05 servername123 systemd: Started MariaDB 10.2.36 database server.
Jan 10 03:30:05 servername123 systemd: Stopping MariaDB 10.2.36 database server...
Jan 10 03:30:07 servername123 systemd: Stopped MariaDB 10.2.36 database server.
Jan 10 03:30:08 servername123 systemd: Starting MariaDB 10.2.36 database server...
Jan 10 03:30:08 servername123 mysqld: 2021-01-10 3:30:08 139859181062336 [Note] /usr/sbin/mysqld (mysqld 10.2.36-MariaDB-log) starting as process 18482 ...
Jan 10 03:30:08 servername123 systemd: Started MariaDB 10.2.36 database server.
cron logs
Quote
Jan 9 03:27:01 servername123 anacron[22631]: Job `cron.daily' started
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29233]: starting certwatch
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29240]: finished certwatch
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[30011]: finished cwp
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp_acme.sh
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[30083]: finished cwp_acme.sh
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp_bandwidth
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30105]: finished cwp_bandwidth
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[29233]: starting logrotate
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30112]: finished logrotate
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[29233]: starting man-db.cron
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30126]: finished man-db.cron
Jan 9 03:27:23 servername123 anacron[22631]: Job `cron.daily' terminated (produced output)
Jan 9 03:27:23 servername123 anacron[22631]: Normal exit (1 job run)
Jan 9 03:28:01 servername123 crond[536]: (root) RELOAD (/var/spool/cron/root)
Jan 9 03:30:01 servername123 CROND[30791]: (root) CMD (/usr/local/bin/svcMonitor)
Jan 9 03:30:01 servername123 CROND[30792]: (root) CMD (/usr/local/bin/svcMonitor-systemd)
Jan 9 03:30:01 servername123 CROND[30799]: (root) CMD (/usr/lib64/sa/sa1 1 1)
Jan 9 03:40:01 servername123 CROND[1167]: (root) CMD (/usr/lib64/sa/sa1 1 1)
Jan 9 03:45:01 servername123 CROND[2379]: (root) CMD (/usr/local/bin/svcMonitor)
Jan 9 03:45:01 servername123 CROND[2380]: (root) CMD (/usr/local/bin/svcMonitor-systemd)
mysql logs
Quote
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Mutexes and rw_locks use GCC atomic builtins
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Uses event mutexes
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Compressed tables use zlib 1.2.7
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Using Linux native AIO
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Number of pools: 1
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Using SSE2 crc32 instructions
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Initializing buffer pool, total size = 40M, instances = 1, chunk size = 40M
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Completed initialization of buffer pool
2021-01-10 3:30:05 140584151996160 [Note] InnoDB: If the mysqld execution user is authorized, page cleaner thread priority can be changed. See the man page of setpriority().
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Highest supported file format is Barracuda.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: 128 out of 128 rollback segments are active.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Creating shared tablespace for temporary tables
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Setting file './ibtmp1' size to 12 MB. Physically writing the file full; Please wait ...
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: File './ibtmp1' size is now 12 MB.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: 5.7.32 started; log sequence number 12347021
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Loading buffer pool(s) from /var/lib/mysql/ib_buffer_pool
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Buffer pool(s) load completed at 210110 3:30:05
2021-01-10 3:30:05 140584771946688 [Note] Plugin 'FEEDBACK' is disabled.
2021-01-10 3:30:05 140584771946688 [Note] Server socket created on IP: '::'.
2021-01-10 3:30:05 140584771946688 [Note] Reading of all Master_info entries succeeded
2021-01-10 3:30:05 140584771946688 [Note] Added new Master_info '' to hash table
2021-01-10 3:30:05 140584771946688 [Note] /usr/sbin/mysqld: ready for connections.
Version: '10.2.36-MariaDB-log' socket: '/var/lib/mysql/mysql.sock' port: 3306 MariaDB Server
2021-01-10 3:30:05 140584349431552 [Note] /usr/sbin/mysqld (initiated by: unknown): Normal shutdown
2021-01-10 3:30:05 140584349431552 [Note] Event Scheduler: Purging the queue. 0 events
2021-01-10 3:30:05 140584101639936 [Note] InnoDB: FTS optimize thread exiting.
2021-01-10 3:30:05 140584349431552 [Note] InnoDB: Starting shutdown...
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Dumping buffer pool(s) to /var/lib/mysql/ib_buffer_pool
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Buffer pool(s) dump completed at 210110 3:30:05
2021-01-10 3:30:07 140584349431552 [Note] InnoDB: Shutdown completed; log sequence number 12347040
2021-01-10 3:30:07 140584349431552 [Note] InnoDB: Removed temporary tablespace data file: "ibtmp1"
2021-01-10 3:30:07 140584349431552 [Note] /usr/sbin/mysqld: Shutdown complete
-------------logs--------------------
10
MySQL / Re: cron.daily - mysql restart every night (How to stop ?)
« on: January 20, 2021, 05:25:55 PM »
any idea?
11
MySQL / cron.daily - mysql restart every night (How to stop ?)
« on: January 10, 2021, 11:48:21 AM »
- I want to stop cron.daily - "mysql restart" command but i dont know how.
(help appreciated. thank you.)
Why ?
i need minimum 2 day uptime for analize mysql conf

https://i.postimg.cc/mDRydFxg/screenshot-274.png
also(more importantly) sometimes these restarts cause 5 minutes mysql downtime

https://i.postimg.cc/GppcvXtL/screenshot-273.png
-------------logs--------------------
email
messages logs
cron logs
mysql logs
-------------logs--------------------
(help appreciated. thank you.)
Why ?
i need minimum 2 day uptime for analize mysql conf

https://i.postimg.cc/mDRydFxg/screenshot-274.png
also(more importantly) sometimes these restarts cause 5 minutes mysql downtime

https://i.postimg.cc/GppcvXtL/screenshot-273.png
-------------logs--------------------
Quote
Anacron job 'cron.daily' on sitename123.com
messages logs
Quote
Jan 10 03:30:01 servername123 systemd: Stopping MariaDB 10.2.36 database server...
Jan 10 03:30:03 servername123 systemd: Stopped MariaDB 10.2.36 database server.
Jan 10 03:30:04 servername123 systemd: Starting MariaDB 10.2.36 database server...
Jan 10 03:30:05 servername123 mysqld: 2021-01-10 3:30:05 140584771946688 [Note] /usr/sbin/mysqld (mysqld 10.2.36-MariaDB-log) starting as process 18309 ...
Jan 10 03:30:05 servername123 systemd: Started MariaDB 10.2.36 database server.
Jan 10 03:30:05 servername123 systemd: Stopping MariaDB 10.2.36 database server...
Jan 10 03:30:07 servername123 systemd: Stopped MariaDB 10.2.36 database server.
Jan 10 03:30:08 servername123 systemd: Starting MariaDB 10.2.36 database server...
Jan 10 03:30:08 servername123 mysqld: 2021-01-10 3:30:08 139859181062336 [Note] /usr/sbin/mysqld (mysqld 10.2.36-MariaDB-log) starting as process 18482 ...
Jan 10 03:30:08 servername123 systemd: Started MariaDB 10.2.36 database server.
cron logs
Quote
Jan 9 03:27:01 servername123 anacron[22631]: Job `cron.daily' started
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29233]: starting certwatch
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29240]: finished certwatch
Jan 9 03:27:01 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[30011]: finished cwp
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp_acme.sh
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[30083]: finished cwp_acme.sh
Jan 9 03:27:22 servername123 run-parts(/etc/cron.daily)[29233]: starting cwp_bandwidth
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30105]: finished cwp_bandwidth
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[29233]: starting logrotate
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30112]: finished logrotate
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[29233]: starting man-db.cron
Jan 9 03:27:23 servername123 run-parts(/etc/cron.daily)[30126]: finished man-db.cron
Jan 9 03:27:23 servername123 anacron[22631]: Job `cron.daily' terminated (produced output)
Jan 9 03:27:23 servername123 anacron[22631]: Normal exit (1 job run)
Jan 9 03:28:01 servername123 crond[536]: (root) RELOAD (/var/spool/cron/root)
Jan 9 03:30:01 servername123 CROND[30791]: (root) CMD (/usr/local/bin/svcMonitor)
Jan 9 03:30:01 servername123 CROND[30792]: (root) CMD (/usr/local/bin/svcMonitor-systemd)
Jan 9 03:30:01 servername123 CROND[30799]: (root) CMD (/usr/lib64/sa/sa1 1 1)
Jan 9 03:40:01 servername123 CROND[1167]: (root) CMD (/usr/lib64/sa/sa1 1 1)
Jan 9 03:45:01 servername123 CROND[2379]: (root) CMD (/usr/local/bin/svcMonitor)
Jan 9 03:45:01 servername123 CROND[2380]: (root) CMD (/usr/local/bin/svcMonitor-systemd)
mysql logs
Quote
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Mutexes and rw_locks use GCC atomic builtins
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Uses event mutexes
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Compressed tables use zlib 1.2.7
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Using Linux native AIO
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Number of pools: 1
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Using SSE2 crc32 instructions
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Initializing buffer pool, total size = 40M, instances = 1, chunk size = 40M
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Completed initialization of buffer pool
2021-01-10 3:30:05 140584151996160 [Note] InnoDB: If the mysqld execution user is authorized, page cleaner thread priority can be changed. See the man page of setpriority().
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Highest supported file format is Barracuda.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: 128 out of 128 rollback segments are active.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Creating shared tablespace for temporary tables
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: Setting file './ibtmp1' size to 12 MB. Physically writing the file full; Please wait ...
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: File './ibtmp1' size is now 12 MB.
2021-01-10 3:30:05 140584771946688 [Note] InnoDB: 5.7.32 started; log sequence number 12347021
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Loading buffer pool(s) from /var/lib/mysql/ib_buffer_pool
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Buffer pool(s) load completed at 210110 3:30:05
2021-01-10 3:30:05 140584771946688 [Note] Plugin 'FEEDBACK' is disabled.
2021-01-10 3:30:05 140584771946688 [Note] Server socket created on IP: '::'.
2021-01-10 3:30:05 140584771946688 [Note] Reading of all Master_info entries succeeded
2021-01-10 3:30:05 140584771946688 [Note] Added new Master_info '' to hash table
2021-01-10 3:30:05 140584771946688 [Note] /usr/sbin/mysqld: ready for connections.
Version: '10.2.36-MariaDB-log' socket: '/var/lib/mysql/mysql.sock' port: 3306 MariaDB Server
2021-01-10 3:30:05 140584349431552 [Note] /usr/sbin/mysqld (initiated by: unknown): Normal shutdown
2021-01-10 3:30:05 140584349431552 [Note] Event Scheduler: Purging the queue. 0 events
2021-01-10 3:30:05 140584101639936 [Note] InnoDB: FTS optimize thread exiting.
2021-01-10 3:30:05 140584349431552 [Note] InnoDB: Starting shutdown...
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Dumping buffer pool(s) to /var/lib/mysql/ib_buffer_pool
2021-01-10 3:30:05 140583850985216 [Note] InnoDB: Buffer pool(s) dump completed at 210110 3:30:05
2021-01-10 3:30:07 140584349431552 [Note] InnoDB: Shutdown completed; log sequence number 12347040
2021-01-10 3:30:07 140584349431552 [Note] InnoDB: Removed temporary tablespace data file: "ibtmp1"
2021-01-10 3:30:07 140584349431552 [Note] /usr/sbin/mysqld: Shutdown complete
-------------logs--------------------
12
How to / Re: How do I get rid of Netdata?
« on: April 25, 2019, 10:19:19 AM »
i dont want to share all my website secrets/stats and informations to netdata inc. stop selling our datas! stop installing 3party spywares to our servers !
i dont have time to delete/change your spyware-centoswebpanel right now.
stop automatically installing spywares on every night update, this is 3. times.
i'm uninstalling it for the third time, and you re automatically install and start it again at every night !!!
i dont have time to delete/change your spyware-centoswebpanel right now.
stop automatically installing spywares on every night update, this is 3. times.
i'm uninstalling it for the third time, and you re automatically install and start it again at every night !!!
13
How to / Re: How do I get rid of Netdata?
« on: April 14, 2019, 09:54:10 AM »
- do you sell our datas or other things to netdata, why you automatically install this shit to my server?
- after this, how can i be sure you dont install any other applications to my server (botnet? cyrpto miners?)
I do not trust you and cwp anymore, i sure that i will delete cwp from my server.
- after this, how can i be sure you dont install any other applications to my server (botnet? cyrpto miners?)
I do not trust you and cwp anymore, i sure that i will delete cwp from my server.
Pages: [1]
