This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
61
SSL / Re: Install Let'sEncrypt for Admin Panel & User Panel Again, 100% Working
« on: January 14, 2019, 01:37:29 PM »
Hello
Share the details snahoot of that error and also
Print the log:
# tail -f /var/log/letsencrypt/letsencrypt.log
Share the details snahoot of that error and also
Print the log:
# tail -f /var/log/letsencrypt/letsencrypt.log
63
SSL / Install Let'sEncrypt for Admin Panel & User Panel Again, 100% Working
« on: January 12, 2019, 07:36:37 PM »
Hello Everybody,
I wrote a blog on http://forum.centos-webpanel.com regarding Let's Encrypt SSL Certificate for CentOS Web Panel when "Letsencrypt Manager" option was exist under Apache Settings >> Letsencrypt Manager >> Install Letsencrypt .
At Present CWP Team has been removed "Letsencrypt Manager" that's why it will not renew any cert automatic . They made Auto SSL by default but Auto SSL grade is B and I'm not satisfied with Auto SSL.
Previous Article Link : http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working/
So Previous Tutorial will not work any more on New version of CWP . And It's very awkward for all when some popular feature has been removed from CWP
N.B: I am using the below cipherlist
https://cipherli.st/
https://mozilla.github.io/server-side-tls/ssl-config-generator/
https://wiki.mozilla.org/Security/Server_Side_TLS
So now I am writing this solution again for all of guys and I hope that it will be 100% working again on your CentOS-Webpanel as mine .
Environment Details:
CPU Model: Intel(R) Xeon(R) CPU X3440 @ 2.53GHz
CPU Details: 2 Core (2527 MHz)
Distro Name: CentOS Linux release 7.6.1810 (Core)
Kernel Version: 3.10.0-957.1.3.el7.x86_64
CentOS-Web Panel version: CWP7.admin
CWP version: 0.9.8.757
RAM: 4 GB
Type: VPS
Install Certbot
Check both are installed or not
To avoid duplicating code create the following two configurations snippets:
Generate SSL using certbot
Backup the original file
Edit the file and paste the code & save it
Check the apache syntax and restart the httpd & reload cwpsrv
Uncomment the module & save
Check the apache syntax again and restart the httpd & reload cwpsrv , If you get any error , Please fix the issue . I didn't get any error
Now Fix The Permission :
User Account >> Fix Permissions
Now Edit the following File and save it as below:
Finally reload the server
Now the Final stage is Here:
For Admin Panel
For User Panel
For Webmail
Now Browse all the link and you will not get any warning
CWP Admin Panel Link (by hostname)
CWP Admin Panel Link: http://host.domain.biz:2030
CWP Admin Panel Link: http://host.domain.biz:2086
CWP Admin Panel SSL Link: https://host.domain.biz:2031
CWP Admin Panel SSL Link: https://host.domain.biz:2087
CWP User Panel Link (by hostname)
CWP User Panel Link: http://host.domain.biz:2082
CWP User Panel SSL Link: https://host.domain.biz:2083

Check your SSL setting:
https://www.ssllabs.com/ssltest/
https://www.sslshopper.com/
Please comment and share , If you have any difficulties
For Any kind of Assistance :
Email: glorency[at]outlook.com
VPS : Dedicated Server: Email Solution
I wrote a blog on http://forum.centos-webpanel.com regarding Let's Encrypt SSL Certificate for CentOS Web Panel when "Letsencrypt Manager" option was exist under Apache Settings >> Letsencrypt Manager >> Install Letsencrypt .
At Present CWP Team has been removed "Letsencrypt Manager" that's why it will not renew any cert automatic . They made Auto SSL by default but Auto SSL grade is B and I'm not satisfied with Auto SSL.
Previous Article Link : http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working/
So Previous Tutorial will not work any more on New version of CWP . And It's very awkward for all when some popular feature has been removed from CWP
N.B: I am using the below cipherlist
https://cipherli.st/
https://mozilla.github.io/server-side-tls/ssl-config-generator/
https://wiki.mozilla.org/Security/Server_Side_TLS
So now I am writing this solution again for all of guys and I hope that it will be 100% working again on your CentOS-Webpanel as mine .
Environment Details:
CPU Model: Intel(R) Xeon(R) CPU X3440 @ 2.53GHz
CPU Details: 2 Core (2527 MHz)
Distro Name: CentOS Linux release 7.6.1810 (Core)
Kernel Version: 3.10.0-957.1.3.el7.x86_64
CentOS-Web Panel version: CWP7.admin
CWP version: 0.9.8.757
RAM: 4 GB
Type: VPS
Code: [Select]
# hostname
host.datahead.biz
# cat /etc/redhat-release
CentOS Linux release 7.6.1810 (Core)
# getenforce
Disabled
# systemctl status firewalld
â firewalld.service
Loaded: masked (/dev/null; bad)
Active: inactive (dead)
Before issuing SSL , You must have proper DNS Records Install Certbot
Code: [Select]
# yum install epel-release (if not installed)
# yum update -y
# yum install certbot Check both are installed or not
Code: [Select]
# yum info mod_ssl openssl In my case, mod_ssl is not installed , No issue if openssl is installed , then it would be okay.To avoid duplicating code create the following two configurations snippets:
Code: [Select]
# vi /usr/local/apache/conf.d/letsencrypt.conf
Alias /.well-known/acme-challenge/ "/usr/local/apache/autossl_tmp/.well-known/acme-challenge/"
<Directory "/usr/local/apache/autossl_tmp/">
AllowOverride None
Options MultiViews Indexes SymLinksIfOwnerMatch IncludesNoExec
Require method GET POST OPTIONS
</Directory>
:xGenerate SSL using certbot
Code: [Select]
# certbot certonly --agree-tos --email admin@datahead.biz --webroot -w /usr/local/apache/autossl_tmp/ -d host.datahead.biz
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for host.datahead.biz
Using the webroot path /usr/local/apache/autossl_tmp for all unmatched domains.
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/host.datahead.biz/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/host.datahead.biz/privkey.pem
Your cert will expire on 2019-02-02. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-leBackup the original file
Code: [Select]
# cp /usr/local/apache/conf.d/ssl.conf /usr/local/apache/conf.d/bak.ssl.conf.orig Edit the file and paste the code & save it
Code: [Select]
# vi /usr/local/apache/conf.d/ssl.conf
<IfModule !ssl_module>
LoadModule ssl_module modules/mod_ssl.so
</IfModule>
Listen 443
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
# Requires Apache >= 2.4
SSLCompression off
# OCSP Stapling, only in httpd 2.3.3 and later
SSLUseStapling on
SSLStaplingCache "shmcb:logs/stapling-cache(150000)"
# Requires Apache >= 2.4.11
SSLSessionTickets Off
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(128000)
#NameVirtualHost server_ip:443Check the apache syntax and restart the httpd & reload cwpsrv
Code: [Select]
# /usr/local/cwpsrv/bin/cwpsrv t
# systemctl restart httpd
# sh /scripts/reload_cwpsrv
Uncomment the module & save
Code: [Select]
# vi /usr/local/apache/conf/httpd.conf
LoadModule ssl_module modules/mod_ssl.so
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so Check the apache syntax again and restart the httpd & reload cwpsrv , If you get any error , Please fix the issue . I didn't get any error
Code: [Select]
# /usr/local/cwpsrv/bin/cwpsrv t
# systemctl restart httpd
# sh /scripts/reload_cwpsrv Now Fix The Permission :
User Account >> Fix Permissions
Now Edit the following File and save it as below:
Code: [Select]
# vi /usr/local/apache/conf.d/hostname-ssl.conf
# vhost_start host.datahead.biz
<VirtualHost *:443>
ServerName host.datahead.biz
ServerAdmin webmaster@datahead.biz
DocumentRoot /usr/local/apache/htdocs/
SSLEngine on
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLCertificateFile /etc/letsencrypt/live/host.datahead.biz/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/host.datahead.biz/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/host.datahead.biz/fullchain.pem
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown
<IfModule mod_suexec.c>
SuexecUserGroup nobody nobody
</IfModule>
<IfModule mod_suphp.c>
suPHP_UserGroup nobody nobody
suPHP_ConfigPath /home/nobody
</IfModule>
<Directory "/usr/local/apache/htdocs/">
AllowOverride All
</Directory>
</VirtualHost>
# vhost_end host.datahead.bizFinally reload the server
Code: [Select]
# /usr/local/cwpsrv/bin/cwpsrv t
# systemctl restart httpd
# sh /scripts/restart_cwpsrv Now the Final stage is Here:
For Admin Panel
Code: [Select]
# vi /usr/local/cwpsrv/conf/cwpsrv.conf
Find the below code :
ssl_certificate /etc/pki/tls/certs/hostname.crt;
ssl_certificate_key /etc/pki/tls/private/hostname.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
And replace with:
ssl_certificate /etc/letsencrypt/live/host.datahead.biz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/host.datahead.biz/privkey.pem;
ssl_protocols TLSv1.2;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH;
:x For User Panel
Code: [Select]
# vi /usr/local/cwpsrv/conf.d/users.conf
Find the below code :
ssl_certificate /etc/pki/tls/certs/hostname.crt;
ssl_certificate_key /etc/pki/tls/private/hostname.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
And replace with:
ssl_certificate /etc/letsencrypt/live/host.datahead.biz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/host.datahead.biz/privkey.pem;
ssl_protocols TLSv1.2;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH;
:x For Webmail
Code: [Select]
# vi /usr/local/cwpsrv/conf.d/webmail.conf
Find the below code :
ssl_certificate /etc/pki/tls/certs/hostname.crt;
ssl_certificate_key /etc/pki/tls/private/hostname.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
And replace with:
ssl_certificate /etc/letsencrypt/live/host.datahead.biz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/host.datahead.biz/privkey.pem;
ssl_protocols TLSv1.2;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH;
:x Now Browse all the link and you will not get any warning
CWP Admin Panel Link (by hostname)
CWP Admin Panel Link: http://host.domain.biz:2030
CWP Admin Panel Link: http://host.domain.biz:2086
CWP Admin Panel SSL Link: https://host.domain.biz:2031
CWP Admin Panel SSL Link: https://host.domain.biz:2087
CWP User Panel Link (by hostname)
CWP User Panel Link: http://host.domain.biz:2082
CWP User Panel SSL Link: https://host.domain.biz:2083
Check your SSL setting:
https://www.ssllabs.com/ssltest/
https://www.sslshopper.com/
Please comment and share , If you have any difficulties
For Any kind of Assistance :
Email: glorency[at]outlook.com
VPS : Dedicated Server: Email Solution
64
SSL / Re: Buy own certificate for my hostname and email SSL/TLS point to server - how ?
« on: January 12, 2019, 07:03:21 PM »
Hey
Use Let'sEncrypt SSL for all domain and it's working fine on my server
New solution for Let'sEncrypt : goo.gl/Ys764T , This is google short link url .
Use Let'sEncrypt SSL for all domain and it's working fine on my server
New solution for Let'sEncrypt : goo.gl/Ys764T , This is google short link url .
65
SSL / Re: how to install letsencrypt for admin panel & user panel ?
« on: January 12, 2019, 07:00:00 PM »This is for Server Hostname SSL settings . At Present CWP Team has been removed Lets Encrypt that's why it will not renew any cert . They made Auto SSL by default but Auto SSL grade is B and I'm satisfied with Auto SSL.
Can you please clarify this? I thought Auto SSL was just a wrapper for letsencrypt?
Editing the hostname (Server Settings / Change Hostname) generates an invalid self-signed certificate. Why has support for auto generated hostname letsencrypt certificates been removed, and is it coming back?
Also, the instructions in the thread "Install Letsencrypt SSL Certificate for your Server Hostname/FQDN, 100% Working" are not valid anymore as they refer to "Apache Settings >> Letsencrypt Manager >> Install Letsencrypt" which doesn't seem to exist anymore.
No , Auto SSL is still exist
New solution for Let'sEncrypt : goo.gl/Ys764T , This is google short link url .
66
SSL / Re: LetsEncrpt wildcard SSL issues.
« on: January 12, 2019, 06:40:48 PM »
Here it is : goo.gl/Ys764T , This is google short link url .
direct link: http://forum.centos-webpanel.com/ssl/install-let'sencrypt-for-admin-panel-user-panel-again-100-working/
direct link: http://forum.centos-webpanel.com/ssl/install-let'sencrypt-for-admin-panel-user-panel-again-100-working/
67
PHP / How to Load PHP extensions Imagick & Exif for Rouncube Webmail
« on: December 27, 2018, 10:41:05 AM »
Hi
I have installed successfully both PHP extensions Imagick & Exif but the extension is not showing in Roundcube Webmail Installer .
Please check the images for reference(s) :

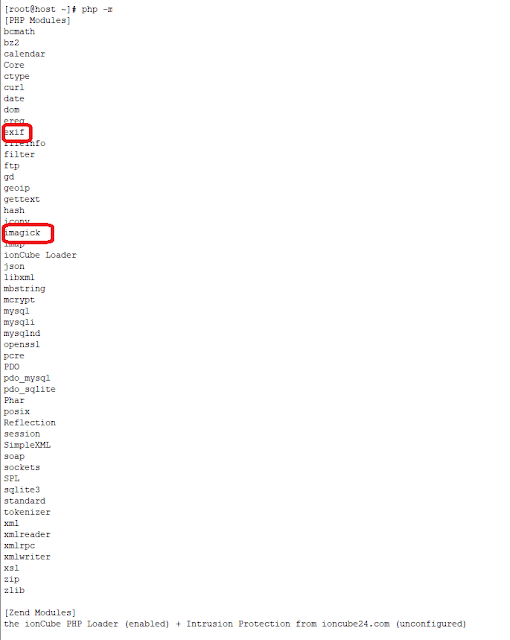
How can i fix this issue ?
Thanks
I have installed successfully both PHP extensions Imagick & Exif but the extension is not showing in Roundcube Webmail Installer .
Please check the images for reference(s) :


How can i fix this issue ?
Thanks
68
SSL / Re: LetsEncrpt wildcard SSL issues.
« on: November 04, 2018, 09:21:44 AM »
I making Proper Document for that solution , Please wait
69
SSL / Re: LetsEncrpt wildcard SSL issues.
« on: November 02, 2018, 08:34:04 AM »
I have installed wildcard LetsEncrypt SSL for my domain using certbot . It's very easy process .
Share your Details like CWP version & domain .
Share your Details like CWP version & domain .
70
SSL / Re: Replace self signed CWP SSL cert on server hostname with letīs encrypt ssl cert
« on: October 18, 2018, 06:19:19 PM »The new module for SSL via Letīs Encrypt actually works just fine, except for the 'custom install - also for server hostname) install.
Using all other options in the module works like a dream, but there is no option on how to get the server hostname, eg. srv1.dmoain.ldt to work as smoothly as the other options in the module...?
Checking around the web, it shows that most people with this problem, canīt find the correct path to put into the box and donīt know if they have to set 2031 in the port setting and actually how to get the Custom Install to setup and replace the CWP generated and self signed SSL cert...
I havenīt found anybody who made this work just by filling out the boxes in the 'custom install' option in the module, but have found an ocean of more or less strange options on how to circumvent the present setup to make it work...
Maybe it would be a good idea to make a step-by-step information for all to follow to avoid many asking the same question here and many other places...?
Must Follow :
http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working/
71
SSL / Re: how to install letsencrypt for admin panel & user panel ?
« on: October 17, 2018, 05:47:14 AM »Check this forum threadThis article is not for admin panel.
http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working//
FYI
This is for Server Hostname SSL settings . At Present CWP Team has been removed Lets Encrypt that's why it will not renew any cert . They made Auto SSL by default but Auto SSL grade is B and I'm satisfied with Auto SSL.
72
SSL / Make Your Server FQDN [Lets Encrypt/Auto SSL] SSL certificate A+ Grade
« on: October 09, 2018, 02:14:33 PM »
Hello Everybody
Hope you are doing well. I am using CWP6.admin in CentOS 6.9 with Lets Encrypt .
But My SSL certificate grade is B and My Cipher list is not so strong.
So I am going use Strong Cipher list and I will show you that how to make your SSL certificate A+ grade .
Visit https://www.ssllabs.com/ssltest/ and Provide your Server FQDN & wait for the result .
You will see that your SSL is not A+ grade .
Login to your server using SSH .
1.Change the directory
#cd /usr/local/apache/conf.d/
2.Backup ssl.conf
3. Edit ssl.conf & paste the below code
#vi ssl.conf
<IfModule !ssl_module>
LoadModule ssl_module modules/mod_ssl.so
</IfModule>
Listen 443
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
# Requires Apache >= 2.4
SSLCompression off
# OCSP Stapling, only in httpd 2.3.3 and later
SSLUseStapling on
SSLStaplingCache "shmcb:logs/stapling-cache(150000)"
# Requires Apache >= 2.4.11
SSLSessionTickets Off
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(128000)
#NameVirtualHost server_ip:443
4.save & close
5. Open httpd.conf file
#vi /usr/local/apache/conf/httpd.conf
Enable the below module , just uncomment
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
6.save & close
6.Restart Apache & cwp server
7. Finally visit https://www.ssllabs.com/ssltest/ & provide your server FQDN , And See result , your server SSL certificate is A+ grade.
Source : Cipherli.st Strong Ciphers for Apache, nginx and Lighttpd
https://cipherli.st/
If you need any further assistance , just post a comment below , i will try to assist you.
Hope you are doing well. I am using CWP6.admin in CentOS 6.9 with Lets Encrypt .
But My SSL certificate grade is B and My Cipher list is not so strong.
So I am going use Strong Cipher list and I will show you that how to make your SSL certificate A+ grade .
Visit https://www.ssllabs.com/ssltest/ and Provide your Server FQDN & wait for the result .
You will see that your SSL is not A+ grade .
Login to your server using SSH .
1.Change the directory
#cd /usr/local/apache/conf.d/
2.Backup ssl.conf
3. Edit ssl.conf & paste the below code
#vi ssl.conf
<IfModule !ssl_module>
LoadModule ssl_module modules/mod_ssl.so
</IfModule>
Listen 443
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
# Requires Apache >= 2.4
SSLCompression off
# OCSP Stapling, only in httpd 2.3.3 and later
SSLUseStapling on
SSLStaplingCache "shmcb:logs/stapling-cache(150000)"
# Requires Apache >= 2.4.11
SSLSessionTickets Off
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(128000)
#NameVirtualHost server_ip:443
4.save & close
5. Open httpd.conf file
#vi /usr/local/apache/conf/httpd.conf
Enable the below module , just uncomment
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
6.save & close
6.Restart Apache & cwp server
7. Finally visit https://www.ssllabs.com/ssltest/ & provide your server FQDN , And See result , your server SSL certificate is A+ grade.
Source : Cipherli.st Strong Ciphers for Apache, nginx and Lighttpd
https://cipherli.st/
If you need any further assistance , just post a comment below , i will try to assist you.
73
CentOS 7 Problems / Re: hostname problem
« on: May 17, 2018, 08:51:52 AM »
Please follow the steps below
##### Set Hostname & FQDN Permanently #####
1. Change Hostname Temporary:
-----------------------------
# show current hostname
[root@server1 ~]# hostname
server1.datahead.biz
# change hostname
[root@server1 ~]# hostname server1.datahead.biz
[root@localhost ~]# hostname
server1.datahead.biz
2. Change Hostname Permanently:
-------------------------------
[root@server1 ~]# hostnamectl set-hostname server1.datahead.biz
[root@server1 ~]# hostnamectl
Static hostname: server1.datahead.biz
Icon name: computer-vm
Chassis: vm
Machine ID: 04ca692cd07d41698530705c118b9b0d
Boot ID: 1e75261cdccc4fd2a412e9d95cbe5a25
Virtualization: xen
Operating System: CentOS Linux 7 (Core)
CPE OS Name: cpe:/o:centos:centos:7
Kernel: Linux 3.10.0-693.21.1.el7.x86_64
Architecture: x86-64
[root@server1 ~]# vi /etc/hostname
server1.datahead.biz
:x
[root@server1 ~]# vi /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
103.56.209.100 server1.datahead.biz server1
:x
[root@server1 ~]# vi /etc/sysconfig/network
NETWORKING=yes
HOSTNAME=server1.datahead.biz
OR
# Created by anaconda
HOSTNAME="server1.datahead.biz"
:x
rDNS is another issues , fix your hostname first , if you need help regarding dns , please reply .
##### Set Hostname & FQDN Permanently #####
1. Change Hostname Temporary:
-----------------------------
# show current hostname
[root@server1 ~]# hostname
server1.datahead.biz
# change hostname
[root@server1 ~]# hostname server1.datahead.biz
[root@localhost ~]# hostname
server1.datahead.biz
2. Change Hostname Permanently:
-------------------------------
[root@server1 ~]# hostnamectl set-hostname server1.datahead.biz
[root@server1 ~]# hostnamectl
Static hostname: server1.datahead.biz
Icon name: computer-vm
Chassis: vm
Machine ID: 04ca692cd07d41698530705c118b9b0d
Boot ID: 1e75261cdccc4fd2a412e9d95cbe5a25
Virtualization: xen
Operating System: CentOS Linux 7 (Core)
CPE OS Name: cpe:/o:centos:centos:7
Kernel: Linux 3.10.0-693.21.1.el7.x86_64
Architecture: x86-64
[root@server1 ~]# vi /etc/hostname
server1.datahead.biz
:x
[root@server1 ~]# vi /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
103.56.209.100 server1.datahead.biz server1
:x
[root@server1 ~]# vi /etc/sysconfig/network
NETWORKING=yes
HOSTNAME=server1.datahead.biz
OR
# Created by anaconda
HOSTNAME="server1.datahead.biz"
:x
rDNS is another issues , fix your hostname first , if you need help regarding dns , please reply .
74
SSL / Re: Install Letsencrypt SSL Certificate for your Server Hostname/FQDN, 100% Working
« on: May 08, 2018, 01:56:42 PM »
Install Letsencrypt by the following :
Apache Settings >> Letsencrypt Manager >> Install Letsencrypt
Before Installing Letsencrypt , Please allow 443 port .
Please upload your snapshot regarding the problem .
Apache Settings >> Letsencrypt Manager >> Install Letsencrypt
Before Installing Letsencrypt , Please allow 443 port .
Please upload your snapshot regarding the problem .
75
SSL / Secure your Webmail with Letsencrypt SSL Certificate , 100% Working
« on: April 19, 2018, 11:14:47 AM »
Hello Guys,
To secure your webmail with Green SSL bar , just follow the steps below describe
1. Follow the Link http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working/
2. Go to "/usr/local/cwpsrv/conf.d/" and open
#vi webmail.conf
server {
listen 2096;
server_name localhost;
ssl on;
ssl_session_timeout 90m;
ssl_certificate /etc/letsencrypt/live/server1.datahead.biz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/server1.datahead.biz/privkey.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
save & exit .
3. Restart your centos webpanel .
4. Now Check https://server1.datahead.biz:2096/
To secure your webmail with Green SSL bar , just follow the steps below describe
1. Follow the Link http://forum.centos-webpanel.com/ssl/install-letsencrypt-ssl-certificate-for-your-server-hostnamefqdn-100-working/
2. Go to "/usr/local/cwpsrv/conf.d/" and open
#vi webmail.conf
server {
listen 2096;
server_name localhost;
ssl on;
ssl_session_timeout 90m;
ssl_certificate /etc/letsencrypt/live/server1.datahead.biz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/server1.datahead.biz/privkey.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
save & exit .
3. Restart your centos webpanel .
4. Now Check https://server1.datahead.biz:2096/

